OpenLDAP LAN Certificates

In this article I will cover the basics of setting up OpenLDAP with self-signed certificate for SSL usage over the LAN network. I use the OpenLDAP docker image but I won't be going into details of the setup.
I'm publishing this because I hope it will help someone else. I struggled for weeks with one error after another on every step of this process, and was close to completely giving up. The official LDAP documentation is 269 pages of useless tehcnical jargon and good guides are few and far inbetween. The learning curve is steep and can a trial of patience!
What is OpenLDAP
Lightwieght Directory Access Protocol (LDAP) is a set of open protocols used to access and modify centrally stored information over a network. It can be used to store a variety of information, sort of like a database except unlike traditional databases LDAP is designed for read and search operations which makes it great for storing user data for identity management and authorization.
OpenLDAP is an open-source implementation of LDAP, and is probably the most widely used by enterprises and hobbyists alike. It is concidered to have a steep learning curve but is very effective. Another popular LDAP server is Windows Active Directory, and Free IPA is promising but is very resource-heavy. Currently nothing comes close to OpenLDAP due to its size and speed.
Some people may argue that containerizing a LDAP server is a bad idea, but I disagree. There are less guides and things get tricky when it comes to hostnames and some configurations but it is not any less secure than a traditional standalone server.
Terminology
- Entry (or object): A 'unit' in an LDAP directory. Each entry is qaulified by its Distinguished Name (DN). Ex: dn: uid=user0,ou=admins,dc=example,dc=com
- Attributes: Pieces of information associated with an entry. Ex. A user's email or address
- objectClass: This is a special attribute which all objects in LDAP must have. The objectClass definition specified which attributes may be modified by clients, but the objectClass itself cannot be removed. Objectclass definitions are stored in schema files.
- Schema: A collection of rules that determines the structure and contents of the directory. This includes attribute type difinitions, objectClass definitions, and more.
- LDIF: LDAP Data Interchange Format. It is a plain-text file for importing or exporting data to and from LDAP servers.
- slapd/slurpd: The main stand-alone daemons of the server. slapd listens for LDAP connections and slurpd propagates information from one slapd database to another.
Software Clients to Access LDAP
- OpenLdap has a command line interface which works just fine
- Apache Directory Studio is my personal favorite, very easy to use
- JXplorer is a classic written in Java
- phpLDAPadmin is an okay server side option but I had difficulty setting it up
Using LDAPS Over LAN
In my case I only want my LDAP server to be accessible from my Local Area Network address, meaning I will assign it no domain name for external access. This means I have to generate a self-signed certificate if I want to use SSL/TLS/LDAPS. Now it's not the worst thing to use regular LDAP over a private network, but a layer of encryption is extra security in the event of a Man in the Middle Attack. It can be a headache to setup though.
There are two options for getting an SSL key signed by a certificate authority: 1. Buy a certificate from an existing authority (eg. Verisign) 2. Declare yourself an authority
I'm going with the latter as it's free and no less secure, and only adds one extra step. I found this guide useful in explaining the underlying concept of self-signed certs.
The Certificate
In order to properly generate a certificate with SSL we will have to follow the below steps:
- Create a private key
- Self-sign it as a root Certificate Authority
- A root certificate is a certificate that belongs to the top node of the trust hierarchy
- Install thie root CA on any device which is going to access the service through SSL
- Note: Sometimes it can be required to install the certificate in multiple locations. Ex firefox for Windows uses a different certificate store than the main system
- Create a certificate for the server
- Sign the certificate with the root CA key
Create the Root Private Key
First create a root key: openssl genrsa -des3 -out rootCa.key 2048 Keep this key very private
The des3 argument creates a password for the key which is optional but recomended.
Standard key sizes are either 1024 or 2048. 4096 is extra and takes 5x more processing power than 2048
Self-Sign the Root Certificate
This only needs to be done once: openssl req -x509 -new -nodes -key rootCa.key -sha256 -days 1024 -out rootCa.pem
You can change the number of days the certificate will be valid for
Import the Root Certificate
An output file rootCa.pem needs to be created for every device you want to connect with the SSL service. Look up a guide on installing certificates for your OS or web server.
Create and Install LDAP Certificate
First we need to create a different private key than above openssl genrsa -out ldap.key 2048
Then generate a certificate used by the signing request: openssl req -new -key ldap.key -out ldap.csr
You be asked a series of questions which for most you can put anything, but the important one is: Common Name (eg, YOUR name) []: 10.0.0.1 This should be the ip, hostname or domain of the service.
Finally, sign the certificate with the CA root key openssl x509 -req -in ldap.csr -CA rootCA.pem -CAkey rootCA.key -CAcreateserial -out ldap.crt -days 500 -sha256
The days here can't be longer than the length of the root certificate
The resultant ldap.key and ldap.cert file are used in the ldap configuration.
NOTE: An alternative to running all those long commands with less prompts generate a key and cert simultaniously from config: openssl req -new -nodes -x509 -days 365 -keyout key.pem -out cert.pem -config openldaps.conf and a config file would look like:
[req]
default_bits = 2048
default_md = sha256
distinguished_name = req_distinguished_name
x509_extensions = v3_req
prompt = no
[req_distinguished_name]
C = US
ST = OK
L = Nowhere
O = MyGroupName
OU = IT
CN = 192.168.1.X # Replace with LAN address
[v3_req]
keyUsage = keyEncipherment, dataEncipherment
extendedKeyUsage = serverAuth
subjectAltName = @alt_names
[alt_names]
IP.1 = 192.168.1.X # Replace with LAN Address
That's all there is for creating the certificates.
Creating A User Directory
Here is the best guide I could find explaining LDAP objects and how to set up a login-system.
Basically use an LDAP client to connect via LDAPS, then set up an "organization unit" OU for users and groups.
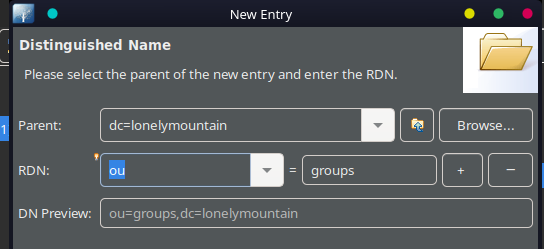
Then create a new POSIX group by adding a new entry under the group. Then add a user with the Organizational Role and simpleSecurity objects. Look at the list of objects to understand which attribute has the information desired for your userbase.
